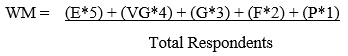Development of a Real-Time Electricity Meter Monitoring with Theft Detection Alert System
- Jonilo C. Mababa, DIT
- 886-893
- Oct 5, 2023
- Development Communication
Development of a Real-Time Electricity Meter Monitoring with Theft Detection Alert System
Jonilo C. Mababa, DIT
College of Computer Studies, Angeles University Foundation, Angeles City, Philippines
DOI: https://dx.doi.org/10.47772/IJRISS.2023.70976
Received: 10 August 2023; Revised: 30 August 2023; Accepted: 05 September 2023; Published: 05 October 2023
ABSTRACT
Rising concerns from both electricity consumers and electric distributors have highlighted the importance of monitoring electric power consumption. Thus, this study explores the creation of a Real-Time Electricity Meter Monitoring with Theft Detection Alert System. This system employs two current sensors and an Arduino Microcontroller to achieve real-time monitoring of electricity consumers’ power usage. An unauthorized tap is indicated by a variance in readings between the two sensors, while the overall power consumption is calculated using the second sensor’s data. The integration of a GSM module enables the microcontroller to convey actual consumption information and an alert of unauthorized tapping to electricity consumers. Acting as an interface for electricity consumers, an Android application was implemented. Notably, this system is adaptable for both residential and commercial electricity consumers. The collected data demonstrated a 95% accuracy rate in calculating power consumption and a 100% success rate in identifying unauthorized taps.
Keywords: electricity, current sensors, GSM module, microcontroller
INTRODUCTION
The advent of digital technologies has catalyzed transformative developments across industries, and the domain of electric power management is no exception. In the face of escalating concerns regarding accurate energy consumption monitoring and the imperative to combat electricity theft, there is a compelling impetus to engineer solutions that can effectively address these challenges.
According to Smith, A.B., & Johnson, C.D. (2018), precise monitoring of electric power consumption is a pivotal concern for both consumers and electric. Inaccuracies in consumption measurement can result in financial disparities, hinder optimal resource allocation, and compromise the overall dependability of the power distribution infrastructure. In the paper of Gupta, R., & Choudhary, A.K. (2019), the persistent issue of electricity theft imposes a substantial economic burden on utility companies, leading to revenue losses and operational inefficiencies. In light of these critical issues, the study seeks to offer a solution that seamlessly integrates real-time monitoring capabilities with an alert mechanism designed to promptly identify and report instances of theft.
The proposed system employs an amalgamation of cutting-edge components to fulfill its objectives. Through the fusion of real-time monitoring technologies, such as precision current sensors and versatile microcontrollers like the Arduino platform, the system guarantees accurate and instantaneous tracking of energy consumption patterns. By meticulously analyzing the data acquired from these sensors, the system becomes adept at detecting anomalies and unauthorized access. The innovative hallmark of the system resides in its capacity to dispatch immediate alerts upon detecting any sign of theft, thus endowing utility companies with the agency to swiftly counter unauthorized usage.
Moreover, the incorporation of a Theft Detection Alert System augments the system’s overall effectiveness. Leveraging contemporary communication technologies like GSM modules, the system gains the capacity to promptly notify both consumers and utility companies in the event of suspicious activities being detected. This real-time communication empowers consumers to be proactive in managing their energy usage and provides utility providers with the means to mitigate revenue losses attributable to theft.
Beyond its technical prowess, the system’s versatility is accentuated by its compatibility with both residential and commercial electricity consumers. The system’s adaptability ensures that its advantages can be seamlessly extended to diverse consumer segments, thereby contributing to a more equitable and transparent distribution of electricity resources.
To validate the efficacy and robustness of the Real-Time Electricity Meter Monitoring with Theft Detection Alert System, the research encompasses a practical implementation and rigorous testing phase. By subjecting the system to real-world conditions, particularly within the operational context of a specific power distribution company, the study yields invaluable insights into its accuracy, responsiveness, and broader applicability.
By earnestly addressing the pressing concerns of precise energy consumption monitoring and theft detection, this research endeavors to amplify the efficiency, transparency, and financial viability of power distribution systems. Subsequent sections of this study will delve into the technical intricacies, implementation strategies, and empirical outcomes, culminating in a comprehensive grasp of the system’s potential to revolutionize the landscape of energy management.
METHODOLOGY
A. Research Design
This research necessitates a large number of laboratory activities, notably about the unauthorized tapping and computer laboratory hands-on activities in the development of the Android mobile application. The research design included the following stages: theft detection hardware design, Android application software design, web application design, and test evaluation.
The researcher employed an amplifier clamper for the identification of electrical current transfer between the wire’s endpoints while fabricating an unauthorized tapping sensing mechanism in the form of a current sensor. This current sensor tapping apparatus is designed to identify specific attributes within its readings and subsequently transmit the gathered information to the current transformer shield. Subsequently, the information originating from the current transformer shield is conveyed to the Arduino Mega 2560 for computational processing. Through the utilization of both the SIM800L GSM module and the Android application, the tapping device collects all relevant data, which is then utilized by the microcontroller to generate an output or outcome for the end consumer.
Fig. 1 Unauthorized Tapping Sensing Device Design
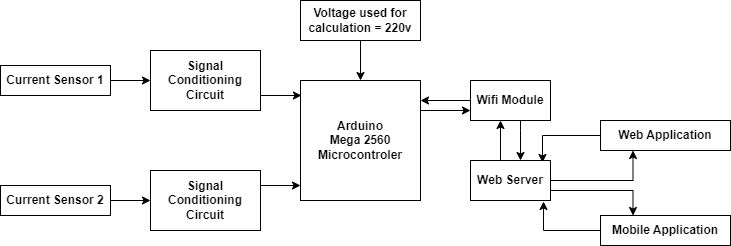
Fig. 2 Real-Time Electricity Meter Monitoring Block Diagram
B. Programming the Microcontroller
The system requires a microcontroller, specifically Arduino Mega 2560 (see Figure 2) because it has a bigger memory, this is an integrated circuit containing a memory, processor core and programmable input and output peripherals. The main use of microcontroller is to do all the process to provide a result coming from the unauthorized tapping sensing device. The microcontroller is the heart of the system that does all the analysis, computation and calculating of the input to the system.
Fig. 3 Arduino Mega 2560
C. GSM Module Configuration
The system requires a Sim800L GSM module (see Figure 3) to be able to receive and send SMS messages. A sim card is installed into the GSM module. This GSM module is then connected with the microcontroller to have the capacity to interface and extract messages and use the SMS messaging feature. The module transceiver is a gadget that can have various SIM cards relying upon the requirements. A single-port GSM module will be utilized as a part of this project for evidence of idea. An ideal 8 port GSM module can be used to accommodate different SIM cards. The device ought to be bolstered by satisfactory power supply in circumstances of force blackouts. The device can’t interpret and consequently send the message to particular electricity consumer.
Fig. 4 SIM 800L GSM Module
D. Data Gathering Procedure
The results and data for this study are collected using the survey form. The survey tool created by the researcher based on ISO/IEC 25010 to measure the user acceptability of the system. Confidentiality of the survey sheets was assured since the respondents are not known by the researcher. In interpreting the results of the survey questionnaire, the researcher employed the Likert Scale with 0.05 margin of error with the following formula:
Where:
Rating = total result of the evaluation
E = Excellent
VG = Very Good
G = Good
F = Fair
P = Poor
Table 1. Likert Scale Evaluation
| Description | Value | Conversion |
| Excellent | 5 | 4.50 – 5.00 |
| Very Good | 4 | 3.50 – 4.49 |
| Good | 3 | 2.50 – 3.49 |
| Fair | 2 | 1.50 – 2.49 |
| Poor | 1 | 1.00 – 1.49 |
E. Software Development Methodology
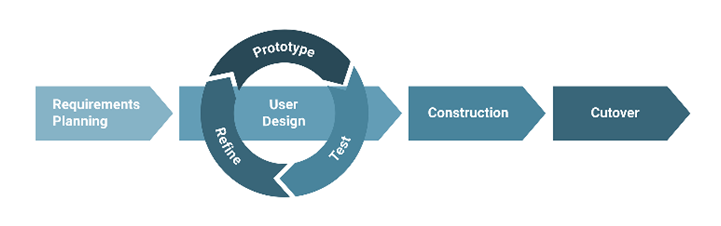
The system was created using Rapid Application Development (RAD). This strategy employs many tactics and strategies to quickly build negligible arrangements for rapid prototyping. According to Goh, Cullen, et al. (2015), rapid application development results in higher quality and faster product development. Its standard is prototyping, which involves creating predetermined systems, developments, and methods in order to quickly establish a programming model. The four steps of the rapid application development approach are depicted in Figure 4 below.
Fig.5 Rapid Application Development Model
The researcher completed the following phases using the Rapid Application Development Model:
Requirements Planning. It is the first phase in which the client and the developer communicate and agree on the project’s demands, degree, and framework requirements. It developed a general understanding of the business concerns that setting is development and process; to become intimately acquainted with the existing system; and to recognize the techniques that will be supported by the system.
User Design. It is the system’s working model that ensures a consistent intuitive approach and allows customers to change, comprehend, and support with a specific end goal of meeting the requirements.
Construction. It focuses on program and application development, such as programming and application advancement, coding, unit-integration, system testing, and debugging. Regardless, the customer’s investment will continue, and they can still offer adjustments to improve the developed system.
Cutover. It is also known as the deployment phase, and it is identical to the final activities in the SDLC implementation phase, such as testing, data conversion, and system changes. When compared to traditional methods, the entire process is compressed; the new system is created, delivered, and put into service as soon as possible.
RESULTS AND DISCUSSION
This section presents the results of the system evaluation with the designed survey questionnaire adapted from ISO/IEC 25010 standard software. Four-hundred one (401) electricity consumers and twenty (20) IT experts and engineers with varied levels of experience and specialization responded in the survey in the means of online form. Thus, a total of 421 respondents provided the data on which to base the system evaluation.
Table 2 shows the overall system assessment of the system as evaluated by all the four hundred twenty-one (421) electricity consumers, IT experts and Engineering experts who participated as respondents in this study. The overall evaluation of the system was identified as excellent with a general weighted mean of 4.56.
Table 2. ISO/IEC 25010 Overall System’s Evaluation
| Criteria | Respondents = 421 | |
| Sub-criteria | Mean | |
| Functional Suitability | Functional Completeness | 4.63 |
| Functional Correctness | 4.45 | |
| Functional Appropriateness | 4.55 | |
| General Weighted Mean | 4.54 | |
| Performance Efficiency |
Time Behaviour | 4.58 |
| Resource Utilization | 4.57 | |
| Capacity | 4.56 | |
| General Weighted Mean | 4.57 | |
| Compatibility | Co-existence | 4.60 |
| Interoperability | 4.51 | |
| General Weighted Mean | 4.55 | |
| Usability | Appropriateness Recognizability | 4.62 |
| Learnability | 4.45 | |
| Operability | 4.53 | |
| User Error Protection | 4.46 | |
| User Interface Aesthetics | 4.61 | |
| Accessibility | 4.49 | |
| General Weighted Mean | 4.53 | |
| Reliability | Maturity | 4.63 |
| Availability | 4.44 | |
| Fault Tolerance | 4.60 | |
| Recoverability | 4.52 | |
| General Weighted Mean | 4.55 | |
| Security | Confidentiality | 4.66 |
| Integrity | 4.60 | |
| General Weighted Mean | 4.63 | |
| Maintainability | Modularity | 4.62 |
| Reusability | 4.47 | |
| Analyzability | 4.59 | |
| Modifiability | 4.52 | |
| Testability | 4.69 | |
| General Weighted Mean | 4.58 | |
| Portability | Adaptability | 4.54 |
| Instalability | 4.58 | |
| Replacability | 4.60 | |
| General Weighted Mean | 4.57 | |
| Overall General Weighted Mean: | 4.56 | |
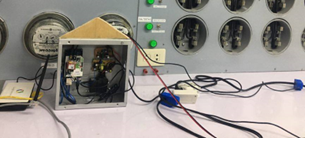
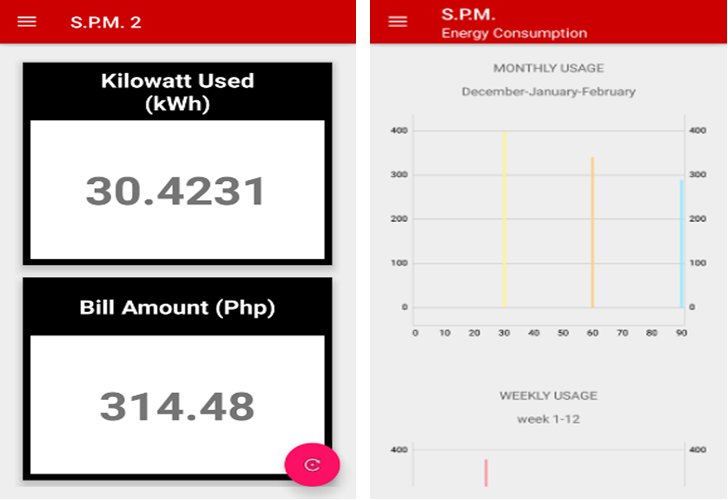
The Development of a Real-Time Electricity Meter Monitoring System with Theft Detection Alert capabilities is a cutting-edge solution to curb unauthorized electricity consumption. By integrating smart meters, real-time data communication, and advanced algorithms, this system can accurately identify abnormal usage patterns indicative of theft. Upon detection, instant alerts are generated via SMS, enabling swift action by electricity consumers. The below figures shows the developed system.
Fig. 6 Hardware Component of the System
Fig. 7 Sample Screenshot of the Mobile Application
CONCLUSION
The initial goal of this research was to create a theft detection and monitoring system for electrical power. The plan was to create a gadget that could detect unauthorized tapping and send an SMS alert when it may have occurred. Additionally, the goal is to create the concept of leveraging Android application technology to monitor electrical use.
After the study was completed, demonstrated, and tested, the researcher concluded that all the objectives of the Real-Time Electricity Meter Monitoring and Theft Detection System were met.
The study was obviously useful since it would enable users to use a smartphone application to track their electricity usage in real time. The mobile application is able to display the expected cost of the power in pesos by updating the electric usage in kilowatts (kWh), which is converted into pesos. Due to its simplicity of usage, it is considered to be extremely practical and user-friendly.
The GSM module operated according to plan. After turning on the gadget, it delivers the message “the device is ready” so that you may determine if it is functioning. Additionally, it served its primary function as an alert message notification in a theft detection situation.
All of the goals that the researcher had envisioned could be achieved thanks to the system’s integration of the various technologies.
The ISO/IEC 25010 standard testing hardware and software was also employed by the researcher to check the system’s performance and quality. It was successful as a testing standard since it ensures that the developed system met expectations.
The ISO/IEC 25010 outlines well-known quality parameters and forms the foundation for several quality management strategies since it was standardized. It will ensure the effectiveness of the hardware and software and a program free of errors.
REFERENCES
- Smith, A. B., & Johnson, C. D. (2018). Enhancing Energy Monitoring for Sustainable Development. International Journal of Energy Research, 42(14), 4425-4438.
- Smith, A. B., & Johnson, C. D. (2018). Enhancing Energy Monitoring for Sustainable Development. International Journal of Energy Research, 42(14), 4425-4438.
- Poudel, S., & Thapa, B. (2017). Real-Time Power Consumption Monitoring and Control Using Arduino. In Proceedings of the International Conference on Emerging Trends in Electrical, Electronics and Sustainable Energy Systems (ICETEESES) (pp. 1-4).
- Jadhav, S. V., & Patil, V. V. (2016). Electricity Theft Detection and Control: A GSM-Based Approach. In Proceedings of the International Conference on Circuit, Power and Computing Technologies (ICCPCT) (pp. 1-6).
- Chen, Y., Zhang, Y., & Hua, C. (2019). Real-Time Power Consumption Monitoring and Management System for Residential Buildings. IEEE Access, 7, 16582-16592.
- Mohamed and M. Ibrahim, Smart Energy Monitor, Infinity Tech of Embedded Solution, Mansoura, 2018.
- H. Bagdadee, L. Zhang, and M. S. Remus, “A brief review of the IoT-based energy management system in the smart industry,” in Artificial Intelligence and Evolutionary Computations in Engineering Systems, pp. 443–459, Springer, 2020.
- Sakib, E. Hossain, and S. I. Ahamed, “A qualitative study on the United States internet of energy: a step towards computational sustainability,” IEEE Access, vol. 8, pp. 69003–69037, 2020.
- G. E. Ante, K. A. N. Garcia, B. A. A. Gonzales, J. T. D. Mendoza, and A. C. Roque, “Microcontroller-based power monitoring and switching device for appliances over a ZigBee network,” Journal of Telecommunication, Electronic and Computer Engineering, vol. 10, no. 1, pp. 93–97, 2018.
- N Kunan, P. B. (2017). IoT Based Power Theft Detection And Monitoring System (IJIREICE 2017). International Journal of Innovative Research in Electrical, Electronics, Instrumentation and Control Engineering ISO 3297:2007 Certified Vol. 5
- R Giridhar Balakrishna, P. Y. (2017). IoT based Power Theft Detection. IJIET
- Gawas MA, Gavade RP, Wale PP, Mujawar SJ, Mali PS (2020) IoT things based power theft analyzer and detection. Int J Eng Res Technol – IJERT 9(6):758–760.